One of the popular Internet services is electronic mail
(e-mail). It is a process of exchanging digital messages from a person to one or
more recipients. Here I will provide an overview of how email systems
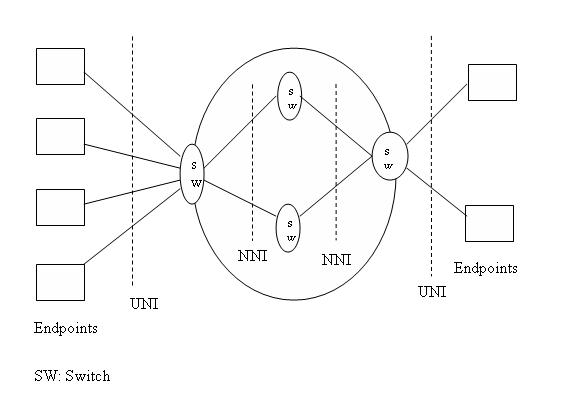
are organized and what they can do. The architecture of the email system is
shown in the below figure,
 |
| Email Architecture |
UA: user agent
MTA: message transfer agent
MAA: message access agent