Multiple Access
When multiple hosts are connecting to a link, we need a multiple access protocol to manage and coordinate access to the link. There exist several protocols to handle access to a shared link. Those are categorized into three groups: channelization protocol, controlled access protocol and random access protocol.
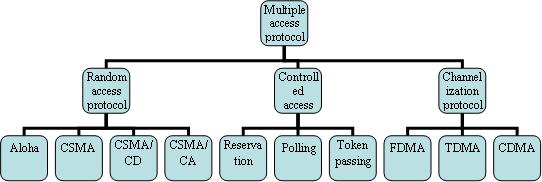 |
| Multiple access protocol |
Random Access
Random access protocols are also known as contention
protocols. In this method, at each moment, a station that has data to send uses
a procedure specified by the protocol to make a decision on whether or not to
send. This decision depends on whether the medium is busy or idle. In the
following sections, we discuss some interesting random access protocols.
ALOHA
The earliest random access method is ALOHA. It was
developed in early 1970. We will discuss two versions of ALOHA here: pure and slotted. They differ with
respect to whether time is continuous, as in the pure version, or divided into discrete
slots into which all frames must fit. The
idea of an ALOHA system is simple: users transmit whenever they have data to be
sent. Since there is only one channel to share, there is the possibility
of collision between frames from different stations. Senders need some
way to handle the collision.
Pure
ALOHA use acknowledgement from the receiver to
know whether a frame is collide or not. If the acknowledgement for a specific
frame does not arrive after a specific time out period then sender assumes that
the frame has been destroyed and resend the frame after some random time (back-off
time).
In slotted
ALOHA the time is divided into slots and force the station to send only at
the beginning of the time slot. The duration of a slot is equal to time
requirement of a frame.
Carrier Sense Multiple Access (CSMA)
To
reduce the probability of collision, the
CSMA protocol was introduced. In CSMA stations are listen to carrier before
start the actual transmission and act accordingly.
If a station determines either a channel is
busy or channel is idle, then it uses the following methods to decide whether
wait or send.
- 1-persistent method
- Non-persistent method and
- p-persistent method
In 1-persistent method, when
a station has data to send, it first listens to the channel
to
check whether anyone else is transmitting at that moment. If the channel is
idle, the station sends its data (with probability 1).
Otherwise, if the channel is busy, the station just waits until it becomes
idle. Then the station transmits a frame.
If
the channel is busy then the station continuously checks the channel until it
is free.
In non-persistent method, when
a station has data to send, it first listens to the channel to check whether
anyone else is transmitting at that moment. If the channel is idle, the station
sends its data. Otherwise, if the channel is busy, the station waits a random
amount of time and then senses the line again. The probability of the collision
is reduce in the case of the non-persistence method.
The p-persistent method is
used if the channel divided into time slots with slot duration greater than or
equal to the maximum propagation time. In this method, after the station determines that the
line is idle it follows these steps:
1.
With probability p, the station sends its
frame.
2.
With probability q=1-p, the station waits for
the beginning of the next time slot and checks the line again.
a. If the line is idle, it goes to step 1.
b. If the
line is busy, it acts as though a collision has occurred and uses the backoff procedure.
Carrier Sense Multiple Access with Collision Detection
(CSMA/CD)
The normal CSMA method does
not specify what to do after a collision. CSMA/CD provide an algorithm to deal
with collision. In this method a station monitors the channel after it sends a
frame, if there is a collision detected then it resend the frame.
Previous : Multiplexing
No comments:
Post a Comment